Browser extensions have become a critical attack vector in modern cybersecurity. While they offer productivity benefits, unmanaged extensions can leak sensitive data, introduce malware, or create compliance violations. Microsoft Intune provides powerful controls for browser extension management, but visibility into these policies across your organization can be challenging. That's where this PowerShell script becomes invaluable.
The Hidden Security Risk in Your Organization
Browser extensions operate with significant privileges - they can read all website data, modify content, and even interact with other applications. Recent security incidents have shown how malicious or compromised extensions can:
- Steal credentials and session tokens
- Inject ads or cryptocurrency miners
- Exfiltrate sensitive corporate data
- Modify banking or financial transactions
- Create backdoors for persistent access
Despite these risks, many organizations lack comprehensive visibility into which extensions are allowed, blocked, or force-installed across their managed devices. If you are using Intune, this is further conflated by the fact that the policy doesn't give the human readable name of whatever extension it's enforcing. This can lead to redundant and conflicting policies.
What This Script Does
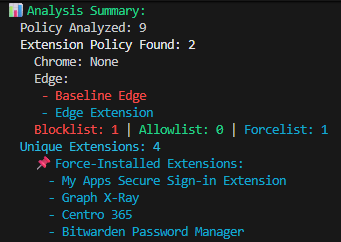
The Get-IntuneBrowserExtensionPolicy script provides complete visibility into your organization's browser extension governance by:
1. Comprehensive Policy Discovery
- Analyzes both legacy Device Configuration policies and modern Settings Catalog policies
- Identifies extension management settings across Chrome and Edge.
- Detects blocklist, allowlist, and force-install configurations
2. Human-Readable Intelligence
Rather than just showing cryptic extension IDs like cjpalhdlnbpafiamejdnhcphjbkeiagm, the script resolves these to actual extension names like "uBlock Origin" by querying the Chrome and Edge web stores.
3. Multi-Format Reporting
Generates three types of outputs:
- CSV files for Excel analysis and Power BI dashboards
- JSON exports for SIEM integration and automated processing
- Executive summaries in plain text for management reporting
4. Audit Trail Compliance
Every analysis includes:
- Timestamped filenames for historical tracking
- Correlation IDs for operational tracing
- Policy creation dates and states
- Complete metadata for compliance requirements
Real-World Use Cases
Security Incident Response
When investigating a potential breach, quickly identify if suspicious extensions could be installed across your organization:
Get-IntuneBrowserExtensionPolicy | Where-Object {$_.PolicyType -notlike '*Blocklist*'}
Compliance Auditing
Generate quarterly reports showing your extension governance posture:
Get-IntuneBrowserExtensionPolicy -IncludeDisabledPolicy -ExportPath "C:\Compliance\Q4-2024"
MSP Multi-Tenant Management
Analyze extension policies across multiple client tenants to identify security gaps and standardize configurations.
Change Management
Track policy modifications over time by comparing exported JSON files to detect unauthorized changes or policy drift.
Key Features That Set It Apart
Performance Optimization
- Fast execution mode with
-SkipExtensionNameResolutionfor automated reporting - Intelligent caching to prevent duplicate web store lookups
- Configurable timeouts and retry logic for reliable operation
Security-First Design
- Validates Microsoft Graph permissions before execution
- Uses read-only operations exclusively
- Implements secure web request handling with domain whitelisting
- No credential storage or exposure
Enterprise-Ready
- Scales from small businesses to large enterprises
- Handles both Windows PowerShell 5.1 and PowerShell 7.x
- Supports pipeline integration for advanced filtering
- Comprehensive error handling and logging
The Business Value
This script transforms browser extension management from a blind spot into a strategic advantage:
- Risk Reduction: Identify unauthorized extensions before they become security incidents
- Compliance Assurance: Maintain audit trails for SOX, GDPR, and HIPAA requirements
- Operational Efficiency: Replace manual policy reviews with automated analysis
- Strategic Planning: Make data-driven decisions about extension governance
Getting Started
The script requires minimal setup:
- Connect to Microsoft Graph with appropriate permissions:
Connect-MgGraph -Scopes "DeviceManagementConfiguration.Read.All"
- Run the analyzer:
Get-IntuneBrowserExtensionPolicy -ExportPath "C:\Reports"
- Review the color-coded console output and exported reports
Conclusion
In an era where browser-based attacks are increasingly sophisticated, visibility into extension governance is not optional - it's essential. This script provides the intelligence needed to secure your browser environment, maintain compliance, and make informed security decisions.
Whether you're responding to an incident, preparing for an audit, or simply wanting to understand your security posture, this tool transforms raw Intune policies into actionable intelligence. The investment of a few minutes running this script could prevent hours of incident response or compliance failures down the road.
Download the script here, run it in your environment, and discover what extensions policies are really running across your organization. You might be surprised by what you find.
For the complete script and documentation, visit the github at https://github.com/fadwen/TechbyJeff/tree/main or connect on LinkedIn.